Blockchain Basics 2021 to know in 2022
Blockchain Basics
1. Introduction
2. Decentralization
3. The Mechanism – How does it work?
4. Cryptography
5. Genesis Block
6. Mining
7. Decentralized Applications
8. Smart Contracts
9. Tokenization
10. Rise of Blockchain
11. Applications into the Future
Blockchain Basics – Introduction
By now, everybody has heard of blockchain and cryptocurrency in one way or the other. Assumptions of this technology range from “Blockchain is the game-changer for the entire human society” to “It’s just another pyramid scheme.” Many argue that Blockchain’s invention is as revolutionary as the burst of the Internet at the dawn of this millennium. For some it’s a staunch truth and for some it is not. Despite the wavering opinions, this technology has given birth to innovation and digital possibilities that have far outperformed the fluctuating thoughts of tech gurus and end-users.
Like any other well-established technology, when we ponder the evolution of Blockchain, it makes us wonder how it all started. We tend to look at the roots, the basics, the humble beginnings of a grandiose entity.
As a wise man called Gordon B Hinckley once said, “You can’t build a great building on a weak foundation.” And that is a reality.
However, the consistent challenge we face, to uncover the truth, is the unlimited repository of myth around this technology available on the internet. This is very misleading and leaves many in a state of confusion. So, before we discuss the applications of Blockchain in the education sector and how it can make our credentials secure, we want to uncover the basics of Blockchain technology that enables this possibility, for a better understanding and adoption.
Satoshi Nakamoto
It all started with the vision of one man, a pseudonymous man per se, Satoshi Nakamoto. The biggest myth till today, even at the time of compiling this guide, is that nobody knows who Satoshi is nor if it’s one man or an entire organization. However, it’s well established and agreed that Satoshi and his team of pioneers have created Bitcoin and the Blockchain technology that powers the entire ecosystem.
In Satoshi’s groundbreaking 2008 whitepaper “Bitcoin: A Peer-to-Peer Electronic Cash System,” he declares:
“A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution. Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to prevent double-spending. We propose a solution to the double-spending problem using a peer-to-peer network. The network timestamps transactions by hashing them into an ongoing chain of hash-based proof-of-work, forming a record that cannot be changed without redoing the proof-of-work. The longest chain not only serves as proof of the sequence of events witnessed, but proof that it came from the largest pool of CPU power. As long as a majority of CPU power is controlled by nodes that are not cooperating to attack the network, they’ll generate the longest chain and outpace attackers. The network itself requires minimal structure. Messages are broadcast on a best effort basis, and nodes can leave and rejoin the network at will, accepting the longest proof-of-work chain as proof of what happened while they were gone.”
Though the existing Bitcoin Blockchain has evolved since inception, the above statement is still the premise on which the world’s leading blockchain works. The same structure is used by Ethereum as well, the second largest blockchain network. In fact, Ethereum is used by many companies to deploy decentralized applications.
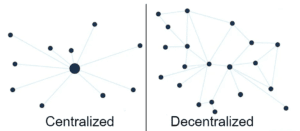
Decentralization
The most important reason for introducing a peer-to-peer based system is to remove the necessity of an intermediary. For example, a bank is considered as a trusted third party or intermediary to save our money as well as perform transactions between different parties. The problem with this system is that this central figure is often prone to attacks, internally or externally.
Blockchain technology negates this possibility. It achieves this result by vesting the responsibility of storing transactions in between peers.

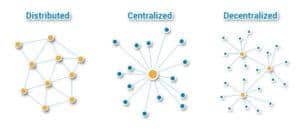
Peers, known as nodes in the blockchain world, maintain the blockchain. They are anonymous & independent, and they function from different parts of the world. Together they create a vast network which is impenetrable or impossible to hack.
The nodes store the data of transactions and maintain the blockchain, thereby creating a distributed ledger. The users of blockchain can access the data even if one node or bunch of nodes exit or lose the chain. This results in continued availability and security of data. To ensure secure transactions, the nodes follow a consensus system. It means that when a new transaction takes place or when a new block is found, every node in the network gets this information. When each node confirms that transaction or that block, it becomes part of the blockchain. This system of reaching an agreement for a transaction is the essence of blockchain and distributed ledger technology. Each blockchain network has its own consensus system.
It’s important to know that as of 2021 there are permissioned &permissionless blockchains, also known as private & public blockchains. There are also hybrid blockchains like XinFin in existence. This has happened due to the rapid growth of the technology and the need for customization across many industries including government & federal institutions.
The Mechanism – How does it work?
So, a ledger is a list of transactions or entries. If this ledger remains under the jurisdiction of one person or institution, then it is a centralized ledger.
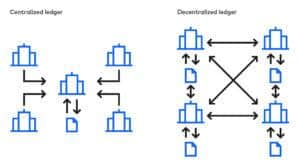
If the same ledger is shared among many, where everybody involved is responsible for managing this ledger and has a copy of the ledger, then it becomes a distributed ledger. If it’s a publicly distributed ledger then it’s a public blockchain. If it’s a privately distributed ledger, it’s a private blockchain.
Let’s dive deeper into it.
From a slightly technical point of view, Blockchain is a data structure. It is a chain of blocks that store transactions and each block is linked to one another in an order. A blockchain, as a file, can be stored on a desktop/laptop or in a database. Different nodes use different types of databases to store the blockchain. For example, Bitcoin’s core client uses Google’s LevelDB database to store blockchain metadata.
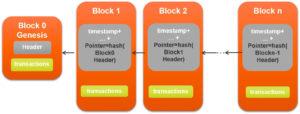
Each block is linked back, referring to the previous block in the chain. Imagine the chain as a vertical stack of blocks placed on top of each other. The first block serves as the foundation. Due to this visualization, we come across terms such as height of block and the top or tip. Height of the block refers to the distance of a block from the first block and the top refers to the most recently added block.
The block created on the top of an existing block is called a “Child Block.” The previous block on which it is placed is called a “Parent Block.” Although a block has just one parent, it can temporarily have multiple children. Each of the children refers to the same block as its parent and contains the same parent hash (address of the previous block) in the “previous block hash” field.
Cryptography
Before we proceed further, it’s important to have a high-level understanding of Cryptography as it is central to blockchain’s operation. Cryptic messages and transactions are as old as mankind. It secures the message between the sender and receiver. In the computer science world, there are various methods of cryptography which enable digital encryption of data. In the blockchain world, we use asymmetric key and hash function methods. In total there are three main types of cryptography. Let’s have a quick look.
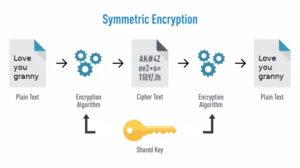
Symmetric Key Cryptography: In this method, the sender and receiver have the same key to encrypt and decrypt the messages. The challenge is for both parties to possess the key to communicate with each other or else the communication is lost.
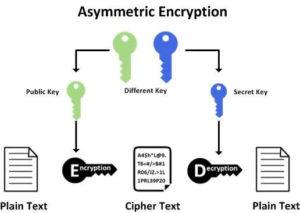
Asymmetric Key Cryptography: In this method, there are two keys, a public key and a private key. A public key is used to encrypt the data and a private key is used to decrypt the data. This is the method used in blockchain technology; however, its application is slightly different.
Instead of encrypting a message or data, we use this method to generate digital signatures. So, the private key holder applies a digital fingerprint to a transaction. Only the key holder can produce this digital signature. Anyone with the access to the public key of the transaction can use them to verify the signature. Essentially, it is this application which is used for credential sharing and verification and it is also critical to the blockchain model.
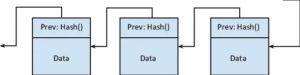
Hash Function
Hash Functions: A plain text is calculated to a hash value with fixed length. It’s used by many operating systems to save passwords. A similar function is used in constructing blocks in blockchain. For those who are not familiar with computer science jargon, it’s ok if you get confused by the word “Hash”. Many of us were initially confused. To provide a clarity and better understanding, let us quickly explain “Hash.”
Hash is a long string of numbers and letters. It is generated by hash algorithms. Let’s say you put in your name in a hash algorithm and generate a hash, the output is going to be a long list of numbers and letters.
For example, for the phrase “We are TruScholar” the resultant hash may be: 5d7c7ba21cbbcd75d14800b100252d5b428e5b1213d27c385e
Even a small change to the phrase will give an output with a totally different hash. Let’s say we change a letter in the phrase, “We are TruScholar.” Now the output is: Js0300uh567sab456es14abki784sau0252da21cbbc7bak1210
As you can see, the results are totally different and a small change in the phrase can affect the hash drastically. This is also the key to tackle fraud and hacking.
So, depending on the hash algorithm of a blockchain, a hash is generated for every transaction as well as the public & private keys of the users. Digital signatures also assume the same format. (Note: The above example is used for demonstrative purposes only. The resultant hash for the phrase will be different in reality.)
Genesis Block
The first block ever created in a block chain is called a genesis block. It acts as the foundation for the corresponding blocks. As each block is back linked to the previous one, the chain will eventually lead to the genesis block. This block is crucial to the entire blockchain.
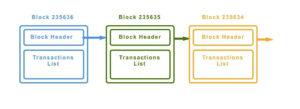
Block Header : So, how can you identify a block? Each block has a header and each block has a hash that’s generated when a block is found. The hash of the block is the identity of the block. Bitcoin uses SHA-256 hash algorithm to generate hash addresses for blocks. Whereas Ethereum uses the Keccak-256 hash.
For example, the hash for the first block or genesis block ever created in 2009, on the bitcoin network is:
000000000019d6689c085ae165831e934ff763ae46a2a6c17
You can confirm it’s existence by checking in sites such as Blockchain info or Blockexplorer by typing it as follows:
https://blockchain.info/block/000000000019d6689c085ae165831e934ff763ae46a2a6c17 This hash was generated by SHA-256 cryptographic hash algorithm. Blockchain networks can use multiple machine languages such as C, C++, Javascript, or Python to generate these hashes.
Contents of a Block Header
It’s understood that the contents of a block are the transactions made on the blockchain at a certain period of time. However, on a block header, you will find more information. Let us understand what other details are present.
Previous Block Hash: Each block has the previous block’s hash added to its header. This results in a backlink to the previous block or the parent block.
Timestamp (time): Along with hash, a timestamp is extremely important for a block. An approximate creation time of a block is critical to its existence. It is the basis of the entire system and provides provenance to a transaction. To quote Satoshi, once again, from his iconic Bitcoin whitepaper:
“The solution we propose begins with a timestamp server. A timestamp server works by taking a hash of a block of items to be time stamped and widely publishing the hash, such as in a newspaper or Usenet post. The timestamp proves that the data must have existed at the time, obviously, in order to get into the hash. Each timestamp includes the previous timestamp in its hash, forming a chain, with each additional timestamp reinforcing the ones before it.”
Merkle Root: Merkle Root is the hash of the root of the Merkle tree. A Merkle Tree is generated as an aggregate of hashes of the block’s transactions. In simple terms it’s a hash generated as the sum (aggregate) of all the transaction hashes in that block.
Version: A version number to track software upgrades. Basically, the version number of the software used to create the block.
Difficulty: It’s a number denoting the difficulty in achieving the target of a block resulting in its creation. It represents the proof-of-work (we will discuss that in a bit) put in to create the block.
Nonce: It’s a random number used in the hash algorithm (which determines the hash of a block) to generate the target of the block.
Now, let’s look at how a block is created or found.
Mining
Let’s imagine a transaction is made in the network. This transaction stays in the network but it’s not necessarily part of a block yet. A new block must be created or rather found for a new transaction to become part of it. So, the process of finding this block is called mining and the nodes or users in the network doing this work are called miners.

Why is it called mining?
Let’s look at a little history. Before we had fiat currency, which is basically paper money, the world used to run on bullion. Coins. We had Gold, Silver, Bronze, and Nickel coins. That means our transactions were valued based on the physical material we used.
Gold is more expensive than most of them because of its various attributes. Now to find this physical material, one should dig through multiple layers of earth and find it.
In the same way, miners need to dig through a complex mathematical algorithm or puzzle to find a block. In Bitcoin blockchain, this complex algorithm is called Proof-of-Work (PoW) algorithm. Even Ethereum uses the same.
It is designed to keep the system secure and serve its purpose. This algorithm is preprogrammed into the blockchain core and it functions autonomously. The difficulty of finding the next block or solving the puzzle increases with every new block created. As an incentive for finding a block and maintaining the blockchain, the successful miner who puts in the work to solve the complex puzzles and finds the block is rewarded with cryptocurrency tokens.
Now, you may have a lingering question such as, “Are these blocks already present?”
Yes, in this sense, they are. All that a miner needs to do is find them. Once found and confirmed by all the nodes, it becomes part of the blockchain. It’s important to understand that solving these puzzles is a lot of work. To solve these puzzles, miners need to own high-end CPUs or stacks of high-end CPUs, which go through every transaction that enters the network while simultaneously solving puzzles to find the next block. Not only does it require a lot of money, but it also requires a lot of electricity.
Latest reports of 2021 suggest that Bitcoin Network consumes 120 gigawatts (GW) per second. Now, that’s a lot of electricity. And it’s also the reason why a hacker or a criminal will find it extremely hard to mess with the blockchain or it’s data.
Proof-of-Stake In the last couple of years, a lot of cryptocurrencies & blockchain networks have adopted Proof-of-Stake (PoS) consensus instead of proof-of-work. Ethereum, for instance, is slowly yet steadily moving to a proof-of-stake consensus model to improve overall efficiency of maintaining the network.
In the proof-of-stake model, there is no need to mine. Instead the nodes who are rewarded the block is based on who has the highest stake. This move is made to reduce the burden on individual nodes or pools of nodes as well as improve the speed of the network. Without getting too deep into, let’s just say that despite the algorithm used, the blockchains will remain secure.
Decentralized Applications
Decentralized applications, popularly known as Dapps, are built on the above concept and executed on blockchains. The data of Dapps is not stored in one server, instead it is distributed among all nodes within the blockchain network. So, loss of data is out of question and retrieving data becomes much easier.
Symmetric Key Cryptography: Smart contracts are an integral part of Dapps executed on a blockchain. They continue to run without any intervention, assuming that they are programmed correctly from the get-go. We will discuss smart contracts in a little bit.
Unlike traditional web, mobile, and native applications, where you can retrieve the code anytime to make changes and launch a new version, Dapps cannot be updated frequently. Because by doing so the blockchain data structure gets disrupted. This ensures that developers are not lazy when they create an application and they need to get it right from the first instance.
Also, that’s the only way to a robust and secure chain. Truscholar is one such application dedicated to use decentralized and blockchain technology to speed up credential verification, recruitment, and student/job applicant processes.
Smart Contracts
As mentioned earlier, smart contracts enable automation on the blockchain. Most smart contracts are native to the blockchain network they are part of, as every blockchain has its own native mechanism to execute smart contracts.
Smart contracts are written using multiple programming languages such as Go, Solidity, JavaScript, and so on.
Decentralized applications use one or more smart contracts. A chain code is used to hold or group similar smart contracts. We will discuss chain codes in depth in a different article.
Basically, smart contracts are programs that run exactly as programmed without any possibility of downtime, censorship, fraud, or third party interface. In one way, all the actions a human intermediary can be programmed into a smart contract. The only difference is that human errors are completely negated and the contract is fully automated.
All the nodes execute the transactions that point to smart contracts, so every node does the same calculations and stores the same values. For example, if there is a smart contract that stores the names and details of everyone attending a party, whenever a new person is added, a new transaction is broadcasted to the network.
For any node in the network to display details of everyone attending the party, they simply need to read the final state of the contract that they have stored. Of course, every transaction requires a different amount of computation and storage; therefore, every transaction has different transaction costs.
While there are many intricacies involved with smart contracts, these are some of the fundamentals of how smart contracts work. At TruScholar, we use Dapps with Smart contracts for storing and verifying the credentials of universities and institutions. That’s how we make our solution fast and autonomous.
Tokenization
We have one more important basic to cover and that’s Tokenization. It’s a major use case of blockchain technology. Tokenization refers to the process of digitally representing and trading an asset. It can also digitally represent your Dapp. Representing a Dapp and starting a new token is called an Initial coin offering (ICO). It had real hype in 2017 and 2018. However, due to various legal issues, it has now stopped.
But, there is a different type of tokenization that is legal, valid, and currently in use. It’s called a Security Token Offering (STO). For example, let’s say you have an apartment. You have rented it out and every month you are getting a small amount of income from it. However, the value of the apartment is much higher than your rent.
So, you decide to monetize your apartment in more ways. In the real world, the possibility of further liquidating and monetizing your asset is very difficult. But with tokenization, it is definitely a possibility in the digital world. This is how it works.
You digitally convert the value of your asset, backed by legal documents, into an STO. Your token now represents your asset in the digital world. Once you have issued your security tokens, you can then start trading them in secondary markets like bitcoin, ethereum, etc., and attract investors.
This way investors can hold a small percentage of your property and you also make money. Like any other trading asset, as your token’s value increases, the investors can sell it to get a good return. Through security tokens, a lot of companies are now looking at raising funds legally. By the way, smart contracts are used here to automate transactions.
Rise of Blockchain
Now that we have covered all the basics, let’s understand how blockchain came to prominence. Initially, when Bitcoin entered the world, nobody took it seriously. One of the reasons for this dismissal is the lack of knowledge behind the entire system and the lack of real-time applicability.
However, overtime, the tech world, the common world and the governments have realized the power of blockchain and the various benefits it brings to multiple sectors.
For instance, in 2017, Russian President Vladmir Putin met with Ethereum founder VitalikButerin to discuss the opportunities of using the technology to develop Russia. Ever since then you can see every other company jumping the blockchain bandwagon. Even big companies such as IBM, J P Morgan, Facebook, Microsoft and many others have their own private blockchains, created in ways suitable to their needs.
Applications into the Future
Currently, blockchain technology is implemented into multiple industries to promote security and automation. Blockchain, when combined with other technologies such as Artificial Intelligence, Machine Learning, or Virtual Reality, can truly bring in a revolution like none other.